-
Comment les cyberattaquants violent-ils votre périmètre de sécurité?
Les cyberattaquants recherchent des failles ou des vulnérabilités dans votre cadre informatique, des aspects qui souvent sont faciles à oublier. Ces failles peuvent se trouver à peu près n’importe où : un mot de passe faible dans votre ordinateur portable d’entreprise ou une pièce jointe de logiciel malveillant dans un courriel d’hameçonnage, par exemple.
-
5 façons de renforcer votre posture de sécurité
Renforcer votre posture de sécurité commence par le choix de pratiques de sécurité qui vous rendent moins sujet aux failles et plus résilient aux attaques. Voici cinq façons de faire basculer la balance en votre faveur.
-
Améliorez votre posture de sécurité grâce à l’aide des experts en cybersécurité de CDW
Chez CDW, nous pouvons vous aider à vous préparer, à vous défendre et à réagir aux menaces à la cybersécurité. Nos équipes d’experts en cybersécurité offrent des conseils et des solutions adaptés à votre cadre organisationnel unique et à vos stratégies de déploiement.
18 avril 2024
5 Strategies to Help Improve Your Security Posture
As cyberattacks become more prevalent, your organization must ready itself with the right practices and technology. Voici cinq façons simples, mais énergiques, qui permettent aux organisations de renforcer leur cyberrésilience, grâce à nos partenaires de cybersécurité.

« Qu’aurions-nous pu faire pour prévenir cela? » est une question courante que les organisations se posent après avoir subi une cyberattaque. Une enquête approfondie est autorisée, les ressources affectées sont réparées et, parfois, les clients sont remboursés.
Heureusement, les organisations munies d’une forte posture de sécurité sont moins susceptibles de poser cette question parce qu’elles ont mis en œuvre des mesures de sécurité visant à réduire les risques d’une cyberattaque réussie.
As cyberattacks become more prevalent, your organization must ready itself with the right practices and technology. Dans ce blogue, nous découvrons cinq façons simples, mais énergiques qui permettent aux organisations de renforcer leur cyberrésilience, grâce aux suggestions de nos experts et de nos partenaires en cybersécurité.
Comment les cyberattaquants peuvent-ils violer votre périmètre de sécurité?
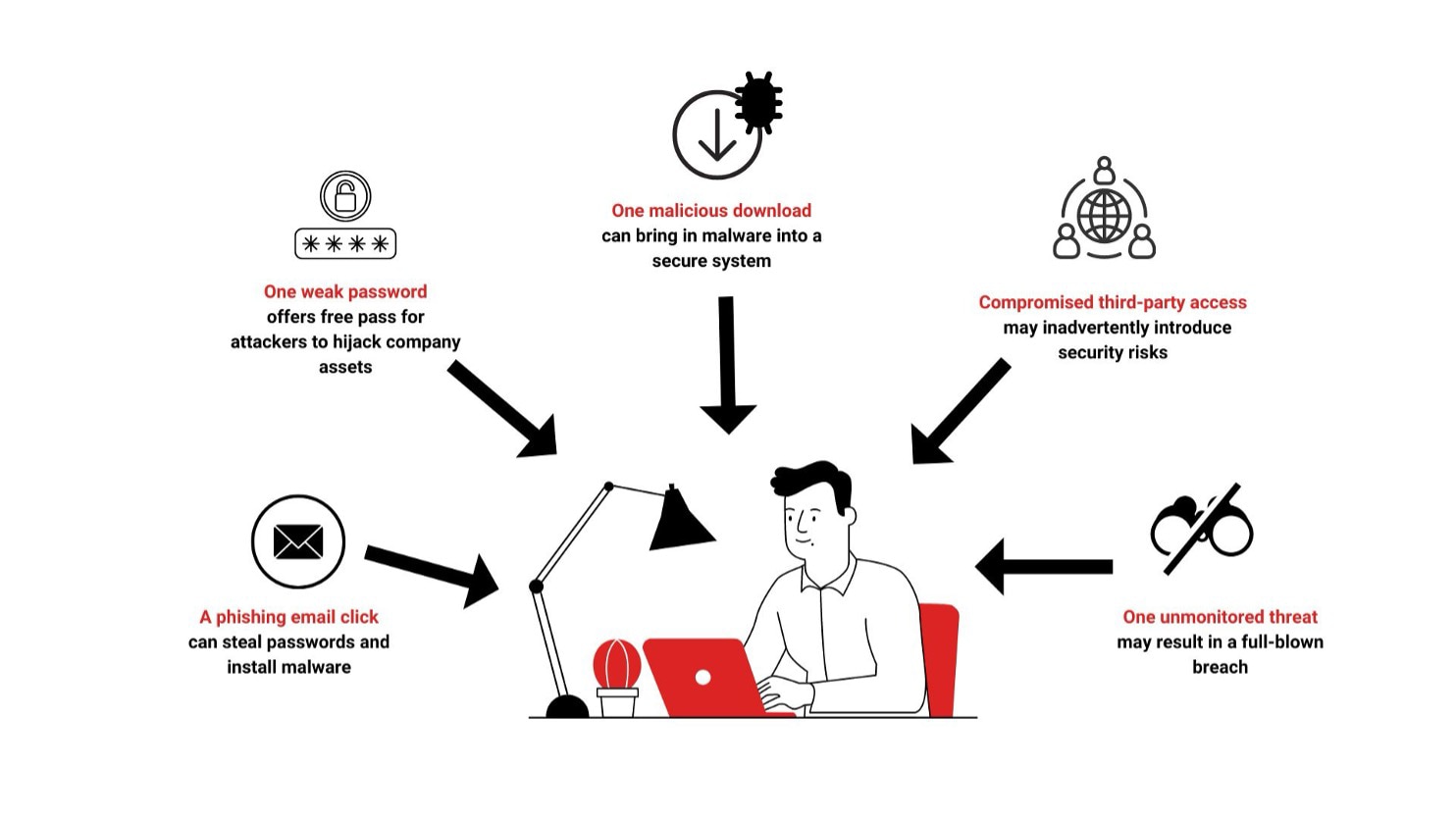
Les cyberattaquants recherchent des failles ou des vulnérabilités dans votre cadre informatique, des aspects qui souvent sont faciles à oublier. Ces failles peuvent se trouver à peu près n’importe où : un mot de passe faible dans votre ordinateur portable d’entreprise ou une pièce jointe de logiciel malveillant dans un courriel d’hameçonnage, par exemple. Au fur et à mesure que votre organisation prend de l’ampleur et devient plus complexe, les identifier et les corriger devient plus difficile.
Parfois, une faille qui laisse entrer les attaquants peut ne pas sembler suspecte du tout. Examinons la présente série d’événements.
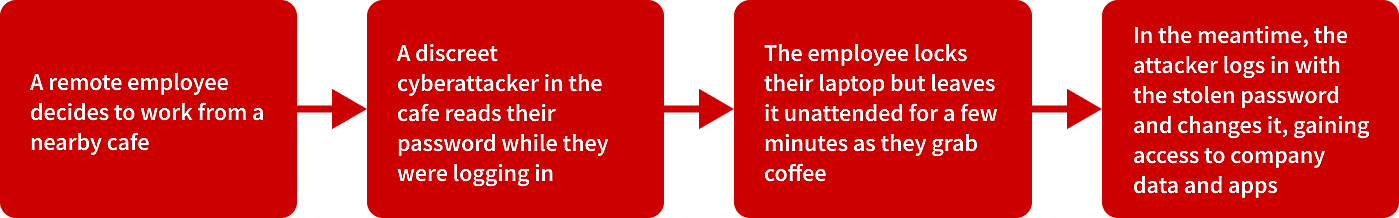
Ici, la faille qui a permis à l’attaquant d’entrer était une combinaison constituée d’un mot de passe faible et de l’absence d’une authentification multifactorielle qui aurait autrement alerté l’employé.
Bien que de travailler à partir d’un café soit tout à fait acceptable, les organisations doivent s’assurer d’avoir mis en place des mesures de sécurité appropriées pour leurs employés. Alors que des milliers d’employés choisissent le travail à distance, que les organisations élargissent leur front numérique et que l’informatique virtuelle devient la norme, les organisations auront plus de lacunes potentielles à couvrir.
Dernièrement, les méthodes des cyberattaquants leur permettant de trouver des failles sont devenues extrêmement sophistiquées. Par exemple, l’étude canadienne sur la cybersécurité de CDW a révélé que 9 à 10 pour cent de toutes les cyberattaques se sont transformées en cyberincidents.
Leurs objectifs communs ne s’étendent pas seulement aux ordinateurs portables des employés, mais aussi à l’ensemble des actifs informatiques, y compris les suivants :
- Applications en logiciel-service (SaaS)
- Terminaux d’API
- Dispositifs de base de données
- Terminaux de dispositif réseau
- Serveurs virtuels
- Dispositifs d’IdO
- Appareils informatiques des clients
En fin de compte, la prochaine attaque pourrait provenir de n’importe où. Les organisations canadiennes, qu’il s’agisse de sociétés privées ou d’institutions du secteur public, doivent s’assurer qu’elles disposent d’une forte posture de sécurité pour se défendre contre les attaques.
5 façons de renforcer votre posture de sécurité
Renforcer votre posture de sécurité commence par le choix de pratiques de sécurité qui vous rendent moins sujet aux failles et plus résilient aux attaques.
Ce processus serait différent pour chaque organisation en fonction de ses besoins et objectifs individuels. Pourtant, il existe des meilleures pratiques courantes qui profiteront à la plupart des organisations pour les aider à garder une longueur d’avance sur les attaquants.
Voici cinq façons de faire basculer la balance en votre faveur.
1. Sécuriser vos terminaux
Tous les appareils électroniques, des ordinateurs portables, aux imprimantes et routeurs réseau en passant par les appareils d’IdO, sont considérés comme des terminaux. À mesure que les organisations grandissent et que de plus en plus de travailleurs travaillent à distance, ces terminaux peuvent devenir plus difficiles à suivre et à gérer.
Étant donné que ces appareils pourraient tous offrir un accès à votre réseau, les pirates peuvent les utiliser comme point d’entrée dans le but de voler des données précieuses. Par exemple, un routeur vulnérable peut servir de point d’entrée au système de fichiers réseau de l’ensemble de l’entreprise.
La sécurisation de vos terminaux empêche les pirates d’entrer dans votre organisation au niveau de l’appareil. CDW s’associe à une variété de fournisseurs de cybersécurité offrant les outils visant à aider à prévenir les attaques.
Absolute Secure Endpoint, qui fait partie du portefeuille de sécurité d’Absolut, peut aider les organisations à intégrer la sécurité à chaque terminal en offrant une visibilité et un contrôle accrus. Le fournisseur offre une technologie de visibilité de terminal étroitement liée au micrologiciel de ce même terminal. Elle aide les équipes informatiques à effectuer le suivi sur la toile des terminaux, même s’ils sont éteints ou ont été altérés.
Cette approche permet aux équipes informatiques et de la sécurité de surveiller les terminaux, de combler les lacunes en matière de sécurité et de permettre l’autoréparation des applications critiques, qui sont toutes essentielles pour maintenir une forte posture de sécurité.
Comment Absolute peut vous aider
- Connexion de terminal toujours active activée grâce à la technologie Absolute Persistence
- Capacités d’autoréparation qui aident les équipes informatiques à mieux gérer le cycle de vie des appareils
- Améliorer la sensibilisation à la conformité en matière de sécurité pour les appareils et les stocks
2. Mettre en œuvre l’authentification multifacteur
L’authentification multifacteur est fondée sur deux facteurs ou plus : quelque chose que vous savez (mot de passe ou NIP), quelque chose que vous avez (une clé physique ou un appareil) ou ce que vous êtes (reconnaissance faciale). Cela peut souvent prendre la forme d’un utilisateur invité à entrer un code d’accès sur son téléphone après avoir saisi son mot de passe original à l’invite de son ordinateur.
Cette étape supplémentaire peut aider à prévenir une attaque si un attaquant vole les identifiants de connexion d’un employé. Le fait que vos employés se connectent au moyen de l’authentification multifacteur peut réduire considérablement les risques d’usurpation d’identité. Cependant, si un attaquant peut inciter l’employé à saisir le code sur son téléphone, il peut être en mesure de compléter lui-même le processus d’authentification multifacteur (AMF).
Nos partenaires chez Yubico ont trouvé des solutions pour résoudre ce problème. Leur solution AMF comprend une clé de sécurité matérielle appelée YubiKey qui prend en charge un large éventail de protocoles d’authentification, ce qui en fait un outil polyvalent pour améliorer la sécurité et assurer l’intégrité de votre organisation sur Internet.
Yubico permet de bénéficier d’une AMF sans mot de passe résistant à l’hameçonnage, ce qui empêche les tentatives de contournement par message texte, authentifiant ou courriel. Leur norme d’authentification FIDO utilise la cryptographie pour empêcher toute utilisation par des cyberattaquants non autorisés. Les clés YubiKey ne stockent aucune donnée et ne nécessitent aucune connexion réseau, batterie ou logiciel client.
Comment Yubico peut vous aider à améliorer votre posture de sécurité
- Améliorez la sécurité de l’authentification grâce à une AMF plus forte, à l’épreuve de l’hameçonnage et prête pour l’avenir
- Utile pour toutes les organisations ayant des besoins de conformité plus stricts, une main-d’œuvre à distance et des postes de travail partagés
- Modèle de déploiement simple destiné aux entreprises qui ont besoin d'un grand nombre de clés physiques
3. Renforcer la sécurité des mots de passe grâce à la gestion des accès privilégiés
Un mot de passe partagé peut créer des vulnérabilités de sécurité, surtout s’il tombe entre de mauvaises mains. Si un collègue n’est pas en mesure d’accéder à une certaine ressource restreinte, il doit demander l’accès par son propre compte plutôt que d’utiliser temporairement le mot de passe de quelqu’un d’autre.
Voici l’idée derrière la gestion de l’accès privilégié (GAP) : associer le bon niveau d’autorisation de sécurité aux identifiants de connexion.
Trop souvent, les mots de passe sont partagés innocemment sur le lieu de travail, mais ils finissent par créer des problèmes pour les administrateurs des TI. La GAP offre un cadre permettant de résoudre ce problème.
Nos partenaires chez Delinea ont conçu une méthode intuitive et évolutive pour mettre en œuvre la GAP à travers la diversité des niveaux d’accès présents dans une organisation.
Le portefeuille de Delinea est basé sur la plateforme Delinea, qui possède fondamentalement un ensemble de capacités partagées, de la découverte continue à l’analyse de vérification, en passant par l’application de l’AMF et l’écosystème d’intégrations.
En haut de gamme, leurs solutions principales sécurisent les identifiants, offrent un accès sécurisé à vérification systématique et rehaussent les privilèges et les droits. Ces cas d’utilisation principaux aident les clients à ajouter des couches de sécurité aux activités privilégiées. La détection des menaces d’identité et la réponse à adopter permettent aux clients de détecter si certaines identités disposent de trop de privilèges ou si certains comptes sont mal configurés, et de remédier à ces problèmes afin de réduire rapidement les risques.
Comment Delinea peut vous aider à améliorer votre posture de sécurité
- Visibilité de bout en bout : Obtenir une nouvelle visibilité sur les autorisations, les configurations et les relations des utilisateurs et des machines
- Privilège dynamique : Gérer toutes les autorisations privilégiées sur place, en nuages multiples et aux terminaux au moyen d’une seule plateforme consolidée
- Sécurité adaptative : Pouvoir prendre en charge tous les types d’environnements de même que l’intégration à grande échelle des fournisseurs
Grâce à la plateforme Delinea, obtenez une nouvelle visibilité sur les autorisations, les configurations et les relations des utilisateurs et des machines en étendant la voûte à tous les utilisateurs. Depuis les voûtes humaines et machines, gérez toutes les autorisations privilégiées, à la fois permanentes et juste à temps (JAT), sur les lieux, dans les nuages multiples et les terminaux, et ce, au sein d’une seule et même plateforme consolidée.
La plateforme Delinea offre une vaste intégration des fournisseurs et offre un moteur qui établit un contexte autour des identités et des actifs. Il fournit des informations à propos de la surface d’attaque afin de soutenir le principe du moindre privilège et ajuste automatiquement la posture de sécurité. L’architecture est à l’épreuve du temps. Elle est conçue pour les environnements hérités et infonuagiques et peut être déployée en périphérie.
4. Identifier et corriger les menaces en temps réel
Our Étude canadienne sur la cybersécurité de CDW found that the average downtime for various types of cyberattacks ranges from 12 to 18 days. La détection et la correction lentes des menaces pourraient être l’une des raisons d’une reprise si longue.
Il existe un besoin urgent d’outils modernes de détection des menaces et de réponses à celles-ci qui permettent de repousser les attaquants plus rapidement. Ces outils peuvent surveiller activement les menaces dans l’ensemble du cyberespace de l’organisation et vous aider à prendre des mesures correctives avant qu’il ne soit trop tard.
L’offre Omnis Cyber Intelligence (OCI) de NETSCOUT peut aider les organisations à déceler des menaces potentielles sans avoir à attendre des jours. Ses fonctions de visibilité en temps réel utilisent l’apprentissage automatique pour analyser le trafic réseau et identifier rapidement les menaces.
OCI intègre des sources de renseignements sur les menaces mondiales permettant de fournir un contexte et d’anticiper les menaces émergentes. Cet outil est flexible et capable de s’adapter à divers environnements réseau, assurant l’efficacité, peu importe la taille ou la complexité de l’organisation. Il rationalise les flux de travail et favorise le travail d’équipe au sein des analystes de la sécurité, améliorant ainsi la réponse aux menaces.
OCI offre une visibilité complète de votre réseau, y compris les centres de données, les centres de colocation, le nuage et les travailleurs à distance. Grâce à une visibilité exhaustive, les adversaires sont détectés à chaque étape de leur attaque, y compris lorsqu’ils entreprennent des actions ultérieures à la violation de l’accès d’un ordinateur. L’attaquant peut explorer votre réseau, se déplacer latéralement et recueillir des données. Sans visibilité de ces actions, les attaques peuvent se poursuivre pendant des mois sans être détectées. Grâce à cette visibilité exhaustive, vous pouvez changer la conclusion de ces attaques à l’aide de la détection précoce et la correction que peut effectuer NETSCOUT OCI.
Comment NETSCOUT peut vous aider à renforcer votre posture de sécurité
- Les capacités avancées d’inspection des paquets réseau offrent une recherche nuancée des menaces.
- La solution s’étend aux centres de données, aux appareils des utilisateurs et à l’infrastructure en nuage de l’entreprise.
- L’évolutivité de l’outil OCI garantit qu’il peut couvrir la surface d’attaque en expansion des organisations engagées dans leurs parcours de croissance numérique.
ESET, un fournisseur de détection et de réponse gérées (MDR), offre les mêmes capacités intégrées à une offre de services gérés. L’entreprise collabore avec les équipes des TI au sein des organisations afin de renforcer leur efficacité en matière de chasse aux menaces et d’intervention.
L’offre de services gérés est utile dans les cas où les organisations ont besoin d’une expertise en cybersécurité sans vouloir embaucher des talents internes. De tels services gérés déchargent les risques liés à la détection des menaces en temps réel tout en renforçant la sécurité de l’organisation.
Comment ESET peut vous aider à améliorer votre posture de sécurité
- Pour examiner les menaces potentielles, l’entreprise tire parti d’une combinaison de capacités d’inspection des menaces d’ESET Inspect et de spécialistes en sécurité œuvrant à l’interne.
- Les clients reçoivent des rapports et des informations exploitables leur permettant d’améliorer leur posture de sécurité.
- Réduire la complexité des mises à niveau de sécurité grâce à l’installation, au soutien et au déploiement gérés.
5. S’assurer que votre réseau ne fait confiance à personne
Considérez votre infrastructure réseau comme le pont qui relie votre organisation au monde extérieur. Elle vous permet de servir vos clients et de travailler avec vos fournisseurs, mais si elle n’est pas protégée, elle peut laisser entrer les cyberattaques.
C’est pourquoi les réseaux deviennent souvent des canaux pour les logiciels malveillants et des points d’entrée pour les exploitations abusives. Pour renforcer la sécurité du réseau, le modèle de sécurité à vérification systématique est devenu un choix privilégié de l’industrie.
Il met l’accent sur la configuration de contrôles d’accès stricts et la validation constante de toutes les demandes d’accès, que ce soit à l’intérieur ou à l’extérieur de l’organisation. L’accent est mis sur l’authentification sécurisée et la prévention des accès non autorisés.
La passerelle WAN RUCKUS (RWG) peut permettre l’amélioration de la sécurité du réseau de votre organisation lors de la mise en œuvre d’une architecture de réseau à vérification systématique. RWG assure une authentification et une surveillance continues, en s’alignant sur le principe de la vérification systématique qui est de ne jamais faire confiance et de toujours vérifier.
Elle s’intègre aux moteurs de politiques et vise à accorder aux utilisateurs l’accès uniquement aux ressources nécessaires, minimisant ainsi les risques d’accès non autorisé. Cette solution peut automatiquement déclencher une réauthentification en cas de violation, maintenir l’intégrité de la sécurité et tenir les cyberattaques à distance.
Comment RUCKUS peut vous aider à améliorer votre posture de sécurité
- Prend en charge les protocoles IPsec et OpenVPN, assurant un transfert de données chiffré et sécurisé sur les réseaux.
- Respecte les normes et les lignes directrices de l’industrie, offrant une solution robuste qui assure un accès au réseau sécurisé et la protection des données.
- Offre la sécurité des cinq piliers de la sécurité organisationnelle : identité, données, appareil, réseau et charge de travail.
Améliorez votre posture de sécurité grâce à l’aide des experts en cybersécurité de CDW
Chez CDW, nous pouvons vous aider à vous préparer, à vous défendre et à réagir aux menaces à la cybersécurité. Nos équipes d’experts en cybersécurité offrent des conseils et des solutions adaptés à votre cadre organisationnel unique et à vos stratégies de déploiement.
Notre centre des opérations de sécurité (SOC) fonctionne 24 heures sur 24/7 jours sur 7/365 jours par année et est constitué d’experts canadiens formés pour gérer les événements de sécurité. Nos services sont soutenus par des experts en sécurité de classe mondiale possédant de nombreuses certifications de l’industrie et de nos partenaires, notamment SOC 1, SOC 2, PCI, ISO 27001 et NIST CSF.
Grâce au soutien continu de notre écosystème de partenaires novateurs, nous offrons les conseils appropriés pour transformer les processus de sécurité en plus de fournir les bons outils pour vous aider à améliorer votre posture de sécurité.

