-
L’augmentation de la fréquence des attaques met la continuité des activités à risque
La surface d’attaque, bien qu’elle diminue en 2024, reste vaste et en constante évolution, car les environnements informatiques sont élastiques et s’élargissent ou rétrécissent en fonction des exigences commerciales, soulignant la vulnérabilité des organisations dotées d’architectures de sécurité inflexibles.
-
En cette période de réduction des coûts des TI, les dépenses de sécurité demeurent une priorité absolue
Malgré les contraintes budgétaires, les organisations continuent de prioriser les investissements en cybersécurité. Selon l’étude 2024, les budgets de sécurité faisant partie intégrante des budgets des TI ont augmenté d’une année à l’autre, pour les organisations de toutes tailles et dans tous les secteurs.
-
Pourquoi la sécurité du modèle à vérification systématique doit-elle inclure la détection et la réponse?
L’adoption de nombreuses technologies de sécurité soutenant l’accès au réseau par la vérification systématique, comme la gestion des identités et des accès et l’authentification multifacteurs, connaît une croissance constante. Mais en ce qui a trait aux technologies de détection des menaces et de réponse, l’adoption a diminué.
-
Les préoccupations en matière de cybersécurité entravent l’adoption du nuage
Les environnements infonuagiques sont devenus les composants informatiques les plus fréquemment attaqués, et l’écart entre l’adoption du nuage et l’investissement dans la sécurité informatique en nuage s’est manifesté par un cyberrisque majeur pour de nombreuses organisations canadiennes.
-
L’IA et l’AA représentent des outils inestimables dans le paysage de la sécurité moderne
Grâce à leur capacité à analyser rapidement de grandes quantités de données, à identifier les tendances et à prédire les menaces futures, l’intelligence artificielle (IA) et l’apprentissage automatique (AA) sont essentiels dans la mise en œuvre de la cybersécurité.
-
Comment lutter contre l’IA antagoniste, armé d’une stratégie d’IA
L’IA peut être une épée à double tranchant en cybersécurité. Bien que l’IA puisse habiliter les adversaires, l’IA peut également être utilisée par les équipes de cybersécurité pour aider à la détection et à la réponse aux menaces en temps réel, automatisant le processus d’identification et de neutralisation des menaces.
-
Recommandations et appels à l’action
Quatre recommandations fondées sur le rapport qui peuvent aider les organisations canadiennes à renforcer leurs défenses.
29 avril 2024
La cybersécurité au centre de l’attention 2024 : Principales priorités pour les organisations canadiennes
Notre étude canadienne 2024 sur la cybersécurité met en évidence l’état actuel de la sécurité des TI et les principaux problèmes auxquels sont confrontées les entreprises canadiennes, et offre des renseignements sur la façon de réagir de manière proactive à l’environnement de menace en constante évolution d’aujourd’hui.

Les cyberattaques deviennent de plus en plus sophistiquées, efficaces et destructrices. Alors que les entreprises canadiennes et les dirigeants des TI cherchent à protéger leurs données et à assurer la continuité de leurs activités, la cybersécurité reste une priorité absolue. Les organisations canadiennes qui adoptent l’IA et les technologies d’apprentissage automatique dans le cadre d’une stratégie complète de cybersécurité se retrouvent mieux outillées pour détecter les cyberattaques et y répondre, et pour répondre au problème de pénuries de personnel qualifié et aux contraintes budgétaires.
Notre étude canadienne 2024 sur la cybersécurité met en évidence l’état actuel de la sécurité des TI et les principaux problèmes auxquels sont confrontées les entreprises canadiennes, et offre des renseignements sur la façon de réagir de manière proactive à l’environnement de menace en constante évolution d’aujourd’hui.
L’augmentation de la fréquence des attaques met la continuité des activités à risque
La surface d’attaque informatique est vaste et en constante évolution
La surface d’attaque des organisations canadiennes est vaste et englobe les applications logiciel-service (SaaS), les API, les conteneurs, les machines virtuelles, les systèmes de stockage, les appareils de traitement de base de données, les outils de réseau, les terminaux et plus encore. La surface d’attaque, bien qu’elle ne s’agrandisse pas et même qu’elle diminue en 2024, reste vaste et en constante évolution, car les environnements informatiques sont élastiques et s’élargissent ou rétrécissent en fonction des exigences commerciales, soulignant la vulnérabilité des organisations dotées d’architectures de sécurité inflexibles.
L’augmentation de la fréquence des attaques met tout en danger
La probabilité que les organisations subissent une cyberattaque demeure élevée. En effet, plus de 60 pour cent des organisations canadiennes signalent au moins une violation de données au cours des derniers 12 mois. En outre, plus de 40 pour cent des organisations de tous les secteurs ont signalé un incident infonuagique. Une forte augmentation du taux d’infection par déni de service (DoS) a également été signalée pour les petites organisations, de 34 pour cent en 2023 à 46 pour cent dans l’étude 2024.
FRÉQUENCE D’ATTAQUE
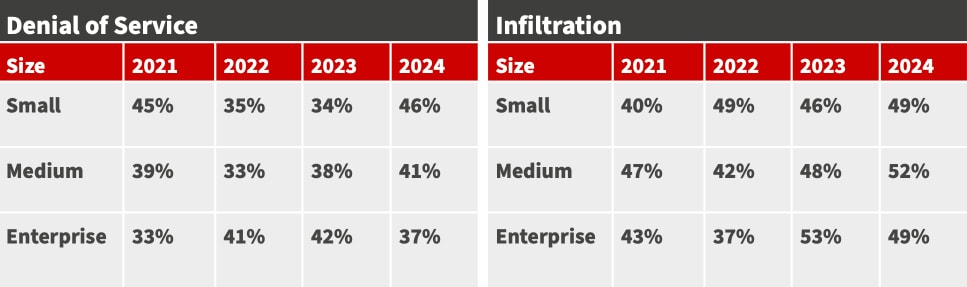
Les organisations sont confrontées à une quantité importante de temps d'indisponibilité
Les cyberincidents perturbent les activités commerciales et mettent les données sensibles en danger, ce qui affecte à la fois la réputation de l’entreprise et le résultat net. Bien que les temps d'indisponibilité soient restés à peu près les mêmes dans l’ensemble en 2024 par rapport à l’étude 2023, ceux liés aux violations et au nuage ont augmenté d’un à trois jours dans l’étude 2024, selon la taille de l’entreprise. Les entreprises canadiennes de toutes tailles ont signalé un temps d'indisponibilité total de deux semaines ou plus dans la plupart des catégories d’attaque.
Les petites organisations ont signalé une forte augmentation des temps d'indisponibilité en raison des attaques par déni de service (DoS) à 18 jours, comparativement aux 12 jours notés dans l’étude 2023. De plus, le temps d'indisponibilité moyen par incident a augmenté en 2024 dans l’ensemble des secteurs, et ce, pour les entreprises de toutes les tailles.
En cette période de réduction des coûts des TI, les dépenses de sécurité demeurent une priorité absolue
- En cette période de réduction des coûts des TI, les budgets de sécurité en pourcentage des budgets globaux des TI ont augmenté dans l’ensemble des secteurs, et ce, pour les entreprises de toutes les tailles.
- Les entreprises sont conscientes que les cybermenaces doivent être combattues afin de réduire l’impact potentiel sur les activités.
- L’adoption de cadres de sécurité peut être un point de départ utile pour améliorer la posture de sécurité globale et la maturité d’une organisation.
La réduction des coûts s’accélère
Compte tenu des défis économiques anticipés et de l’instabilité financière en 2024 et au-delà, les organisations continuent de réévaluer leurs priorités en matière de dépenses. Par conséquent, les entreprises canadiennes passent à des technologies plus rentables, et les budgets des TI ont diminué partout au Canada par rapport à l’étude 2023.
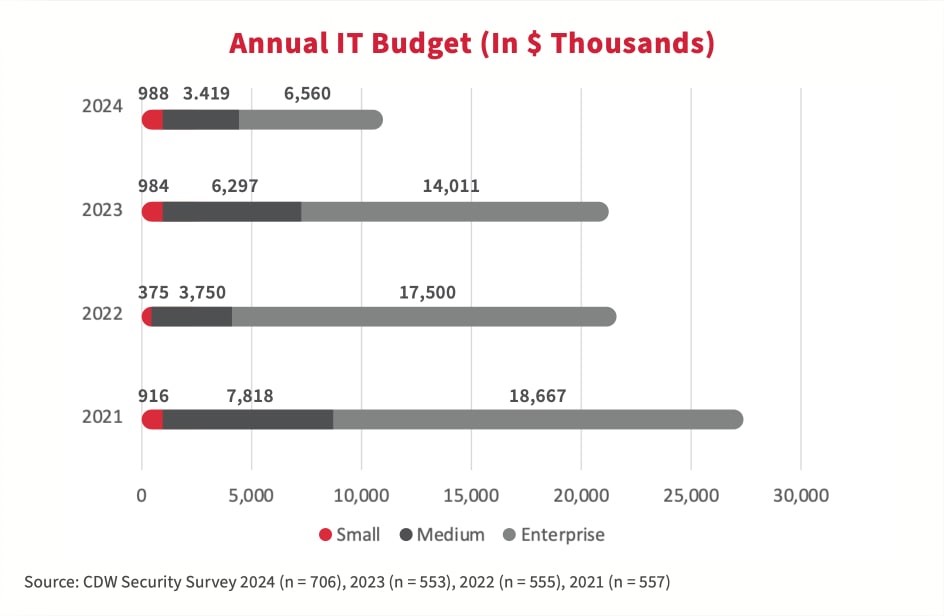
Les dépenses de sécurité demeurent une priorité
Malgré les contraintes budgétaires globales, les organisations continuent de prioriser les investissements en cybersécurité. Selon l’étude 2024, les budgets de sécurité faisant partie intégrante des budgets des TI ont grandi proportionnellement d’une année à l’autre, pour les organisations de toutes tailles et dans tous les secteurs.
Pourquoi est-il risqué de sous-financer la sécurité?
Bien que les dépenses de sécurité en pourcentage du budget des TI aient augmenté, les budgets de sécurité globaux en dollars absolus sont en baisse. Pourquoi est-ce un problème? Avec moins d’argent disponible à dépenser pour la sécurité, les organisations pourraient ne pas être en mesure de se tenir au courant des dernières menaces et technologies, ce qui les rend vulnérables aux attaques. De plus, alors que les membres de l’équipe de sécurité des TI sont épuisés, font face au cycle continu de détection, d’intervention et de rétablissement des violations, cette portion du personnel peut ressentir un épuisement physique et mental, du stress et une baisse du moral.
Pourquoi les cadres de sécurité sont-ils nécessaires?
L’étude 2024 a montré qu’une adoption accrue des cadres de sécurité constitue une première étape importante vers l’amélioration de la maturité. Le NIST CSF ou d’autres cadres mettent l’accent sur une approche fondée sur le risque de la cybersécurité, aidant les organisations à identifier, évaluer et prioriser les risques de cybersécurité. En concentrant d’abord leurs ressources sur l’atténuation des risques prioritaires, les organisations peuvent utiliser plus efficacement les budgets limités. De plus, ces cadres comprennent des mécanismes permettant de mesurer et d’évaluer l’efficacité des efforts de cybersécurité. En démontrant des résultats mesurables, les organisations peuvent justifier la valeur des dépenses de sécurité pour les parties prenantes.
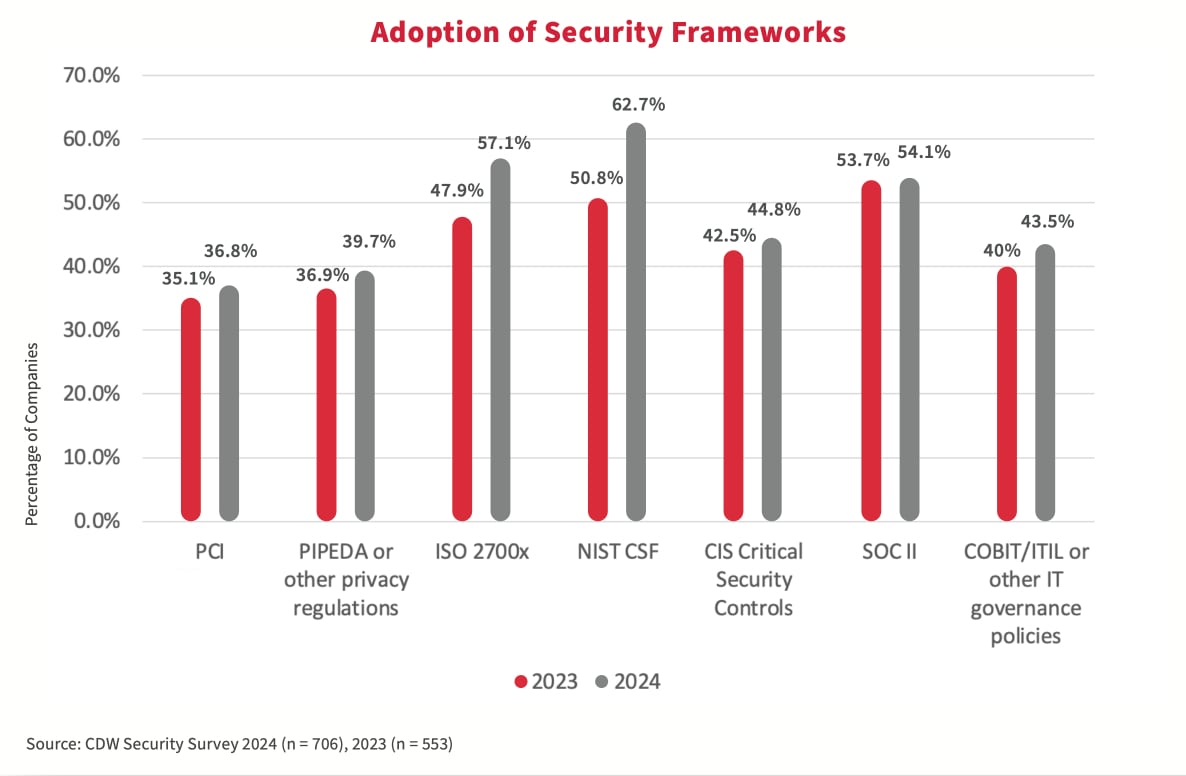
Pourquoi la sécurité du modèle à vérification systématique doit-elle inclure la détection et la réponse?
- À l’ère du nuage, la sécurité fondée sur le modèle à vérification systématique a rapidement gagné en popularité.
- Bien que l’accès avec vérification systématique (zero-trust access, ZTA) constitue un élément essentiel le modèle de sécurité à vérification systématique, il ne devrait pas être le seul point de mire.
- La détection et la réponse aux menaces sont des mesures tout aussi importantes pour assurer une sécurité complète et atteindre les objectifs à long terme de la stratégie de défense à vérification systématique.
Avantages du modèle à vérification systématique
Basé sur le principe de « ne jamais faire confiance, toujours vérifier », la vérification systématique garantit que chaque utilisateur, appareil et flux réseau est authentifié et autorisé avant d’accéder aux ressources. Le modèle de sécurité à vérification systématique est particulièrement avantageux pour les organisations qui ont investi dans des services infonuagiques afin de soutenir le travail hybride, la mobilité des employés et l’innovation commerciale. La confiance inhérente n’est jamais accordée automatiquement, et les architectures évolutives peuvent être facilement étendues aux appareils et aux réseaux, améliorant la visibilité et le contrôle, et offrant une meilleure détection et réponse aux menaces.
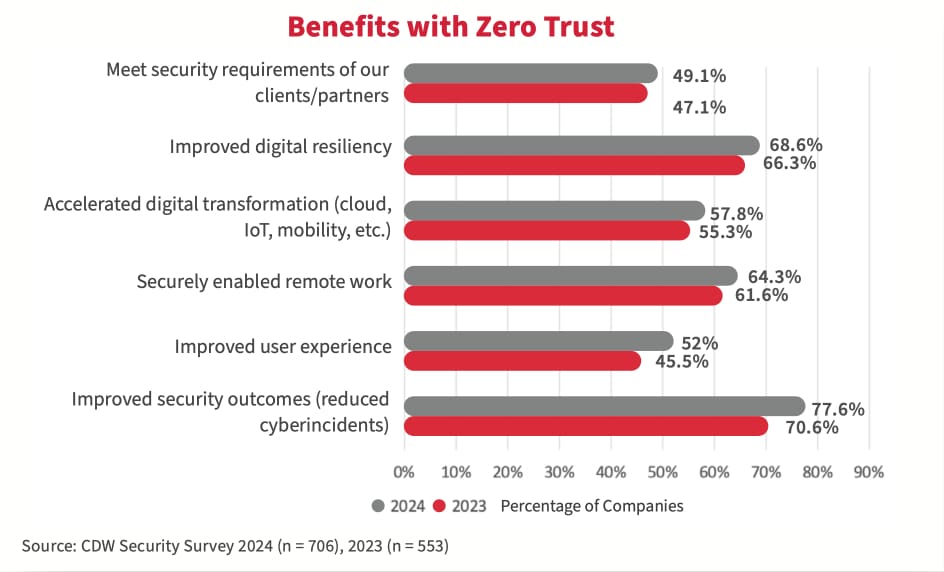
Écarts dans les politiques de sécurité soutenant la vérification systématique
Le modèle à vérification systématique réduit le risque de violation des données en s’assurant que seuls les utilisateurs et les appareils autorisés peuvent accéder aux données sensibles. Il améliore également la visibilité et le contrôle du trafic réseau, permettant aux organisations de détecter et de réagir aux menaces plus rapidement. Cependant, lorsque nous examinons l’adoption de politiques de sécurité qui soutiennent une stratégie de défense à vérification systématique, les organisations ont beaucoup à faire pour profiter du deuxième avantage.
Écart dans les technologies soutenant la détection et la réponse aux menaces
L’étude a montré qu’il existe une croissance constante dans l’adoption de nombreuses technologies de sécurité soutenant l’accès au réseau à vérification systématique, comme la gestion des identités et des accès et l’authentification multifacteurs. Toutefois, en ce qui a trait aux technologies de détection des menaces et de réponse (SIEM, XDR, SOAR), l’adoption a diminué. Le fait de se concentrer uniquement sur l’accès à vérification systématique (ZTA) pour la prévention des menaces, sans investir dans la détection et la réponse aux menaces, peut entraîner un faux sentiment de sécurité. Par exemple, si une menace interne ou une attaque sophistiquée par hameçonnage réussit à contourner cette barrière, l’organisation reste vulnérable.
Au cours des trois dernières années, de nombreuses organisations canadiennes ont indiqué que l’environnement infonuagique public était le composant informatique le plus directement touché par les attaques de cybersécurité. Par conséquent, par rapport à l’étude 2023, moins d’organisations ont conservé leurs données confidentielles et secrètes dans le nuage public. La principale raison citée par 74 % des répondants à l’étude 2024 était leur préoccupation concernant la sécurité.
Les préoccupations en matière de cybersécurité entravent l’adoption du nuage
- Les organisations canadiennes considèrent l’environnement infonuagique public comme le composant le plus directement touché par un incident de cybersécurité.
- Les solutions ponctuelles ne sont pas la réponse.
- Une approche efficace visant à combler les lacunes en matière de sécurité informatique en nuage doit tenir compte de l’ensemble de l’écosystème infonuagique, garantissant que tous les aspects du nuage, de sa conception à son utilisation, sont sécurisés.
Le nuage est attaqué
Les environnements infonuagiques sont devenus les composants informatiques les plus fréquemment attaqués, et l’écart entre l’adoption du nuage et l’investissement dans la sécurité informatique en nuage s’est manifesté par un cyberrisque majeur pour de nombreuses organisations canadiennes.
Les cyberattaques ont érodé la confiance en la sécurité informatique en nuage
Les attaquants utilisent une variété de méthodes pour cibler le nuage – tout, du piratage infonuagique au cryptopiratage en passant par les rançongiciels qui ciblent le stockage infonuagique. Conséquemment, de nombreuses organisations canadiennes se sont senties flouées par la sécurité informatique en nuage. Selon l’étude 2024, 35 pour cent des répondants ne pensent pas que la migration de leurs charges de travail informatiques vers le nuage public a répondu à leurs attentes en ce qui a trait à la sécurité.
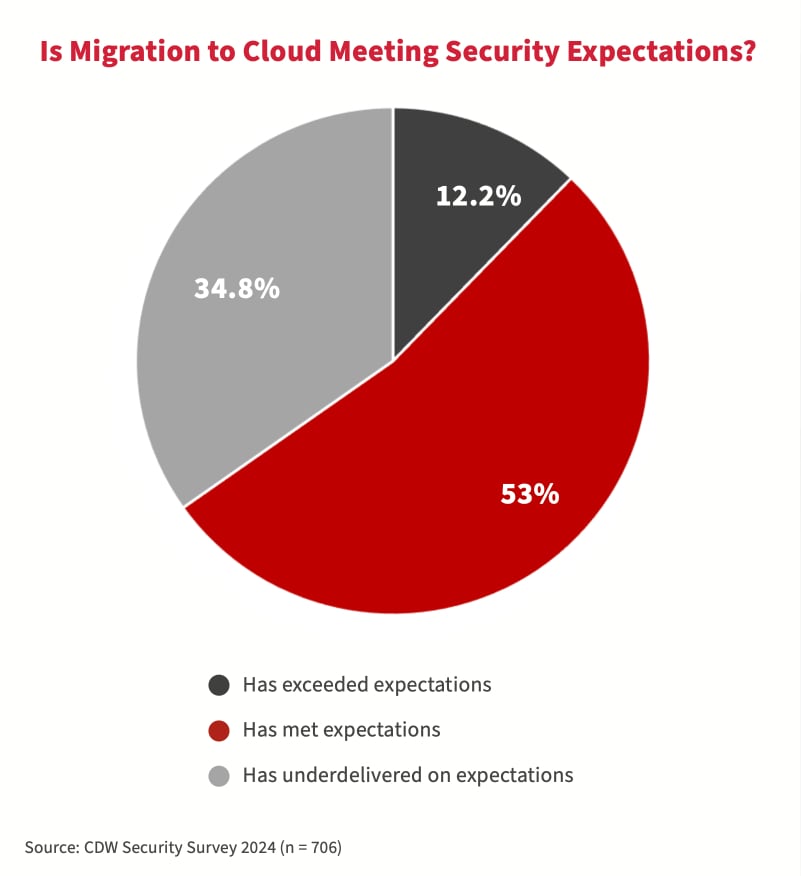
Au cours des trois dernières années, de nombreuses organisations canadiennes ont indiqué que l’environnement infonuagique public était le composant informatique le plus directement touché par les attaques de cybersécurité. Par conséquent, par rapport à l’étude 2023, moins d’organisations ont conservé leurs données confidentielles et secrètes dans le nuage public. La principale raison citée par 74 % des répondants à l’étude 2024 était leur préoccupation concernant la sécurité.
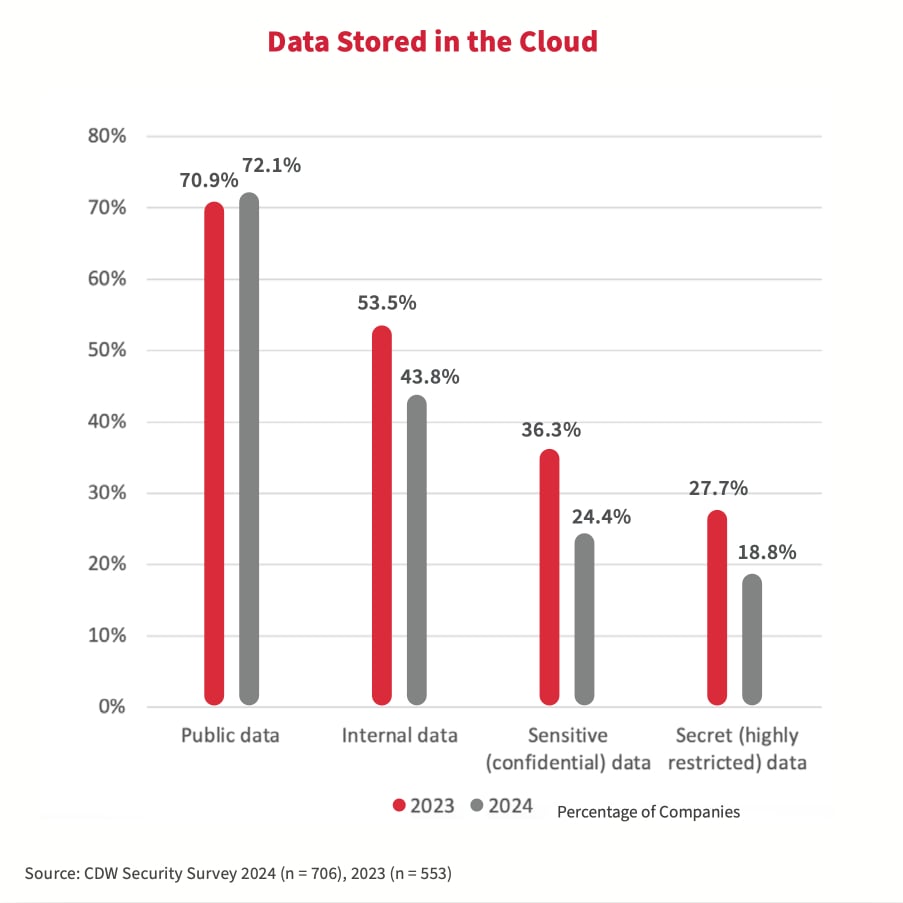
Pourquoi l’investissement dans la technologie n’a pas amélioré les résultats en matière de sécurité
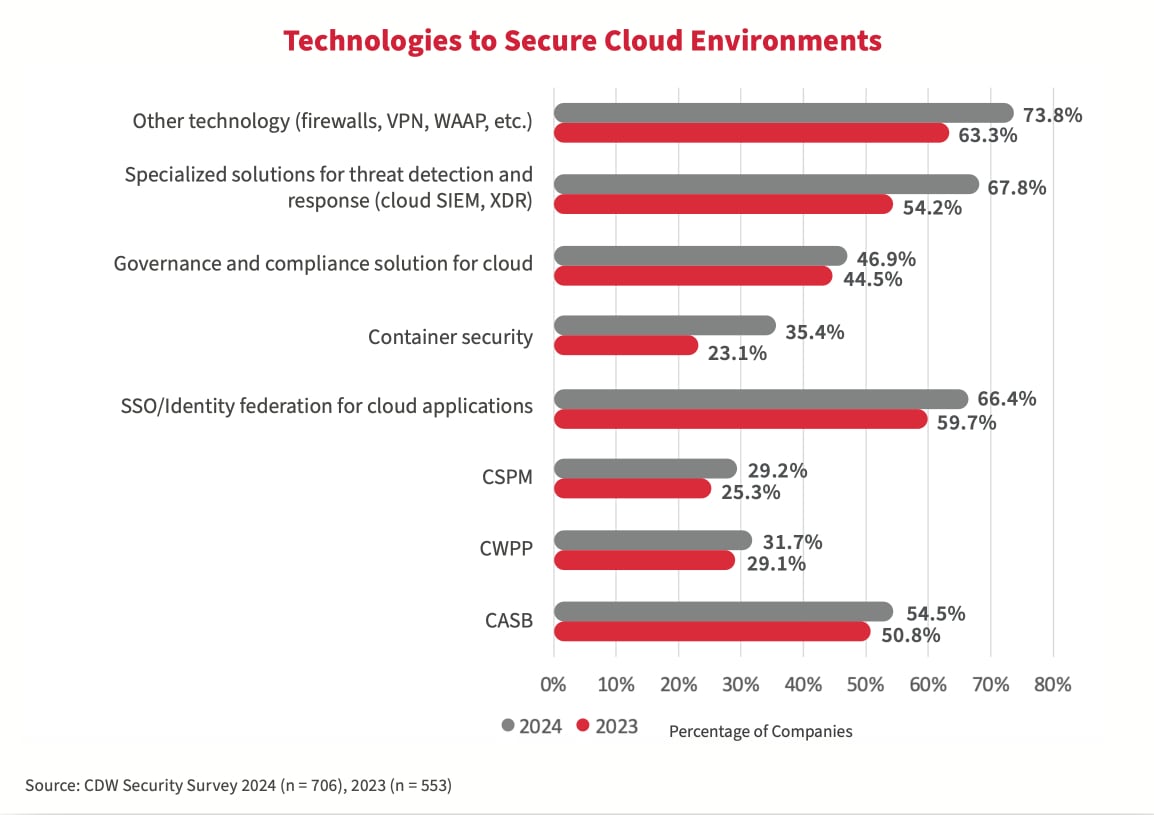
Comparativement à l’étude de 2023, l’adoption des technologies de sécurité informatique en nuage (solutions ponctuelles) a augmenté. Cependant, les données de l’étude 2024 ne montrent pas une réduction significative des incidents de sécurité infonuagique par rapport à l’année précédente. Pourquoi pas? Les solutions ponctuelles répondent à des cas d’utilisation spécifiques plutôt qu’à l’architecture infonuagique globale. Une stratégie plus efficace tient compte de l’ensemble de l’écosystème infonuagique, garantissant que tous les aspects du nuage, de sa conception à son utilisation, sont sécurisés. Il implique également une surveillance continue et une adaptation aux menaces changeantes.
L’IA et l’AA représentent des outils inestimables dans le paysage de la sécurité moderne
- Grâce à sa capacité à générer du texte semblable à celui de l’humain, ChatGPT a démontré la puissance de l’IA d’une manière tangible et accessible.
- ChatGPT a démontré que l’IA et l’apprentissage automatique (AA) peuvent être appliqués efficacement à un large éventail de cas d’utilisation, y compris la cybersécurité.
- Le succès de ChatGPT a accéléré le développement de nouvelles technologies et applications d’IA, ce qui a suscité un intérêt pour l’IA pour les entreprises canadiennes, créant ainsi une boucle de rétroaction positive.
Une approche rentable de la cybersécurité
Grâce à leur capacité à analyser rapidement de grandes quantités de données, à identifier les tendances et à prédire les menaces futures, l’intelligence artificielle (IA) et l’apprentissage automatique (AA) sont essentiels dans la mise en œuvre de la cybersécurité. Ils peuvent également s’adapter à l’évolution des paysages et des menaces informatiques, et, malgré un investissement initial important, peuvent fonctionner avec des ressources limitées, ce qui les rend inestimables face aux menaces croissantes, aux pénuries budgétaires et aux paysages informatiques en évolution rapide.
L’étude de 2024 a montré que l’IA/AA en sécurité informatique constitue une priorité pour de nombreuses organisations canadiennes.
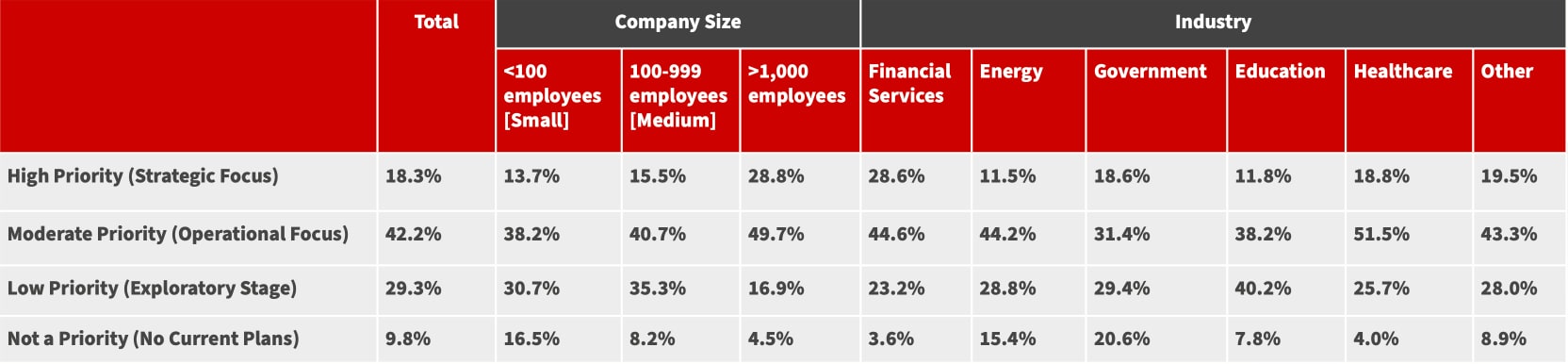
Avantages de l’IA/AA en cybersécurité
L’IA/AA peut améliorer la sécurité et rationaliser les opérations en réduisant considérablement les alertes faussement positives, et en améliorant l’efficacité des opérations de sécurité et les temps de réaction face aux incidents grâce à des processus automatisés de détection et de réponse aux menaces. Ces technologies peuvent également compenser pour les pénuries de personnel qualifie en donnant aux équipes de sécurité la possibilité de gérer des charges de travail plus importantes sans avoir à embaucher du personnel supplémentaire.
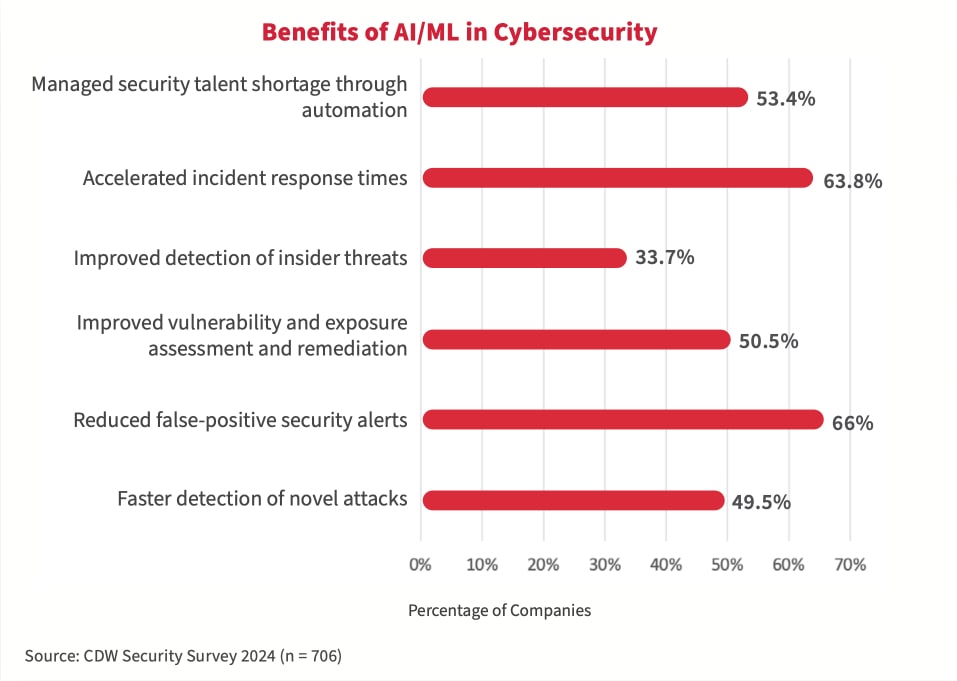
Comment lutter contre l’IA antagoniste, armé d’une stratégie d’IA
- L’IA et l’AA rendent les cybercriminels plus efficaces que jamais, ce qui nécessite des défenses de cybersécurité robustes, elles aussi basées sur l’IA.
- Les organisations qui adoptent les technologies d’IA et d’apprentissage automatique peuvent automatiser la détection et la réponse aux menaces, prédire les menaces potentielles et gérer les pénuries de personnel qualifié.
- Une stratégie complète basée sur l’IA permet de s’assurer que l’IA défensive est utilisée efficacement et de manière responsable contre l’IA offensive ou antagoniste.
Impact de l’IA antagoniste
L’étude 2024 a montré que les organisations canadiennes entretiennent de graves préoccupations concernant le risque que l’IA rende leurs adversaires plus puissants. Les trois principaux risques cités comprennent la possibilité pour les cyberattaquants d’automatiser le processus de découverte et d’exploitation des vulnérabilités (58,4 pour cent), d’identifier de nouveaux vecteurs d’attaque (50,3 pour cent) et d’accélérer le développement de nouvelles souches de logiciels malveillants (42,6 pour cent).
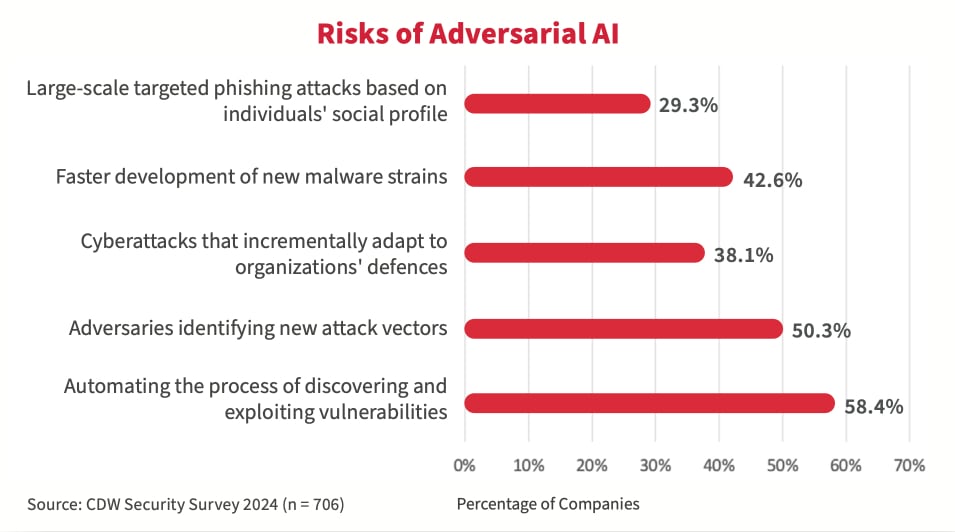
L’IA antagoniste par rapport à l’IA défensive
L’IA peut être une épée à double tranchant en cybersécurité, servant les rôles d’attaquants et de défenseurs. Bien que l’IA puisse habiliter les adversaires, l’IA peut également être utilisée par les équipes de cybersécurité pour aider à la détection et à la réponse aux menaces en temps réel, automatisant le processus d’identification et de neutralisation des menaces. L’IA peut également être utilisée pour prédire les menaces potentielles en fonction des données et des modèles historiques, permettant de profiter de mesures de sécurité proactives. Cependant, la majorité des répondants au sondage croient que le développement de l’IA/AA antagoniste dépassera le développement de l’IA/AA défensive qui doit offrir une protection contre les attaques.
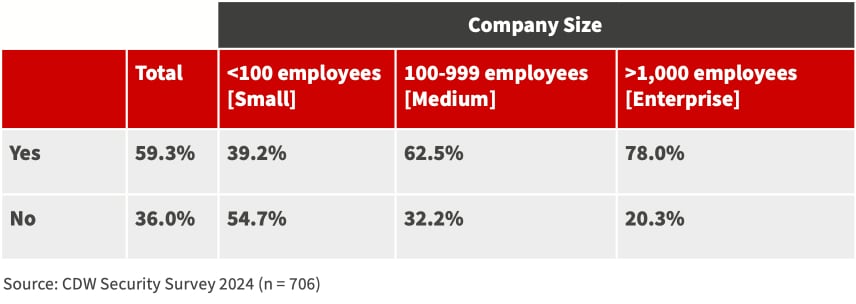
Pourquoi une politique d’IA est-elle une nécessité?
Une politique d’IA à l’échelle de l’organisation doit décrire la position de l’organisation en regard de l’IA, y compris son utilisation, sa gestion et ses considérations éthiques. Elle doit également définir les rôles et les responsabilités, en s’assurant que tous les membres de l’organisation comprennent leur rôle dans la mise en œuvre et le maintien d’une stratégie d’IA. Selon l’étude 2024, 59,3 pour cent de toutes les organisations canadiennes travaillent à la création d’une politique de sécurité concernant l’utilisation de l’IA.
POLITIQUE D’IA EN PLACE
Recommandations et appels à l’action
I. Prioriser la détection et la réponse dans le cadre d’une stratégie de défense à vérification systématique (zero trust architecture, ZTA)
Bien que la ZTA soit un aspect central d’une stratégie de sécurité holistique de vérification systématique, elle ne devrait pas monopoliser l’attention. Les mécanismes robustes de détection et de réponse aux menaces sont tout aussi cruciaux. Les organisations doivent prioriser tous ces domaines pour renforcer leur posture de sécurité et atteindre les objectifs à long terme de la stratégie de défense à vérification systématique. En mettant en œuvre des technologies de pointe, en favorisant une culture d’intervention proactive et en mettant constamment à jour les politiques, les entreprises peuvent assurer une sécurité complète et des opérations résilientes face aux cybermenaces en évolution.
II. Renforcer la confiance envers le nuage
Les responsables des TI et de la sécurité doivent adopter le modèle de responsabilité partagée, où le fournisseur de services infonuagiques (FSI) assume la responsabilité de la sécurité du nuage, tandis que le client est chargé d’assurer la sécurité à son extrémité. Les cadres de sécurité doivent être renforcés par une approche fondée sur le risque et appuyée par des contrôles d’accès rigoureux. De plus, l’établissement d’un système complet de gestion de l’identité et de l’accès (identity and access management, IAM) permettra de s’assurer que seules les personnes autorisées ont accès aux données sensibles. Les outils de surveillance infonuagique constituent l’épine dorsale des mesures de sécurité efficaces, tandis que les alliances avec les experts en sécurité comblent les lacunes en matière de compétences et améliorent les compétences en matière de sécurité informatique en nuage.
III. Créer une stratégie complète d’IA pour la sécurité
Tirer parti de l’IA pour la sécurité implique l’élaboration d’une stratégie globale, l’établissement de politiques et de gouvernance, l’investissement dans la formation sur l’IA, la mise en œuvre de solutions de sécurité par l’IA, ainsi que la surveillance et l’évaluation du rendement de l’IA. En prenant ces mesures, les responsables des TI et de la sécurité peuvent tirer efficacement parti de l’IA au sein dans leurs stratégies de sécurité, améliorant leur capacité à détecter les menaces de sécurité et à y réagir.
IV. Mettre en œuvre un cadre de sécurité efficace
Bien que les contraintes budgétaires puissent poser des défis, elles n’ont pas à empêcher les organisations d’améliorer leur maturité en matière de sécurité. Une fois les cyberrisques évalués et documentés, ils peuvent être gérés efficacement par un cadre de cybersécurité comme NIST CSF et ISO 2700x. Ainsi, une approche structurée de la gestion du risque de cybersécurité est assurée en établissant les contrôles et les mesures de sécurité nécessaires, et en aidant les parties prenantes à comprendre le programme de cybersécurité et son efficacité. De cette façon, les organisations peuvent améliorer leur posture de sécurité et assurer la résilience de leurs opérations.

